Did you celebrate a special woman on International Women’s Day?
Did you celebrate a special woman on International Women’s Day?
Did you celebrate a special woman on International Women’s Day?
Daylight Savings Time begins on Sunday, March 9th at 2AM. Please adjust your clocks accordingly.
The transition to Daylight Saving Time (DST) in the spring, commonly known as “springing forward,” involves setting clocks ahead by one hour. This change can disrupt our internal body clocks, leading to various health and safety concerns. In consideration of your well-being, we would like you to be aware of the following risks of Daylight Savings Time.
Risks Associated with Spring Daylight Saving Time:
Strategies to Mitigate These Challenges:
Are you interested in supporting health and safety initiatives here at Menno Place? The Menno Home Joint Occupational Health and Safety committee (JOHS) is inviting employees to join one of two new subcommittees. No prior experience is required.
The two new committees are:
The goal of the MSI/VP subcommittee is to foster a proactive and supportive environment that minimizes musculoskeletal injuries and promotes employee well-being. The subcommittee will be led by a JOHS representative.
Primary responsibilities of the MSI/VP subcommittee will include:
The primary responsibilities of the Wellness committee will be to promote employee wellbeing by developing and implementing programs that support physical, mental and emotional health for employees, providing health resources etc.
If you would like to be considered for either of these committees please fill out the form below.
To: All Menno Apartments Staff
From: Jessy Manhas
Date: March 13, 2025
Re: MENNO APARTMENTS – HEU-CBA – PHASED IN APPROACH
The HEU-CBA Agreement will be initiated at Menno Apartments with a phased in approach. Phase I will be effective March 25, 2025. This includes all non-monetary provisions.
You can find the HEU-CBA Agreement on the HEU website at: https://heu.org/collective-agreements/community-health/menno-apartments . The next phases will be communicated once an agreement is made with the union.
If you have any questions, you can contact the Chief Shop Steward, Megan Wadham at mewadham@telus.net.
Regards,
Jessy Manhas
Manager of People and Culture
We are excited to introduce two new members to our finance team! Please join us in extending a warm welcome to Sukhdeep and Rupinder as Payroll Business Partners at Menno Place.
Learn practical applications to identify risk factors of violence and de-escalation techniques at a Violence Prevention Workshop on Monday, March 10, 2025. Space is limited. Register soon!
Dear Menno Place Employees,
Earlier this week, your 2024 T4 slips were emailed to the same address on file for your payroll pay notification.
Please note the following:
Important Reminder: The password to open your T4 slip is the same as the password used to access your payroll pay notifications.
MPP pension adjustment (PA) statements were mailed by Canada Post last week to employees who have not opted for electronic delivery from MPP.
Make sure your personal information is up to date
We also want to remind you of the importance of keeping your personal information up to date.
Thank you for your work in providing excellent resident and family-centred care as Menno Place.
This week we prayed for Garry Janzen and his work as the Life Enrichment Coordinator for Menno Home and Menno Hospital.
Leonard shared some thoughts from 1 Timothy 4:7, “Train yourself to be godly” and we prayed for the recreation team in the apartments.
The history of Pink Shirt Day in Canada includes a story of kindness. In 2007, in Berwick, Nova Scotia, after a new student at their school was bullied for wearing a pink shirt, two grade 12 students bought 75 pink shirts and encouraged their classmates to wear pink. The next day they went to distribute the shirts and to their surprise the majority of students arrived wearing pink!
Why is Pink Shirt Day Important?
Pink Shirt Day is an annual event in Canada that raises awareness and funds for anti-bullying programs. It’s celebrated on the last Wednesday of February. This year Pink Shirt Day falls on Wednesday, February 26th. This day raises awareness about the awful effects of bullying – at home, at school and in the workplace – and highlights the simple steps we can take to stop bullying in its tracks. On Pink Shirt Day we remember that when we lift each other up everybody benefits. In a world where you can be anything, be kind.
How to get involved:
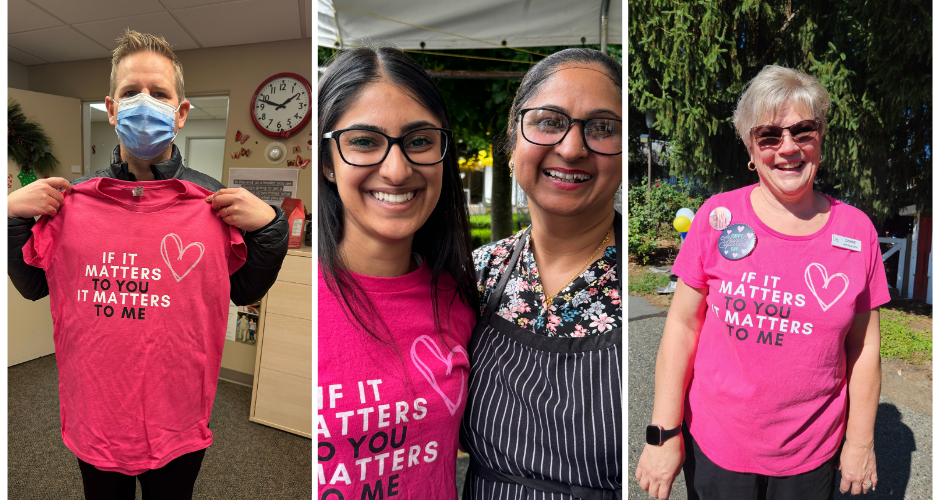
Find ways to practice kindness and support someone who is suffering by clicking here.
These are some strategies:
Additional information
If you experience bullying in the workplace please contact your manager. If you would like to speak to someone confidentially, FSEAP (the employee and family assistance program) is available to all Menno Place staff.
To access FSEAP services 24/7/365 – call 1.800.667.0993
USE OF MATERIALS
All materials available on the www.MennoPlaceStaff.com website are published for the sole purpose of keeping informed those individuals who work on the Menno Place campus. These materials may be shared with others who are also connected to the Menno Place campus in this same way. No content or material may be used or shared in any other context without the written permission of the Menno Place Director who oversees communications.


